Overview:
Attacks by ransomware are a big issue for businesses, and the severity of these attacks is getting worse. Microsoft's Incident Response team recently investigated the BlackByte 2.0 ransomware attacks, revealing their alarming velocity and damaging nature.
Findings:
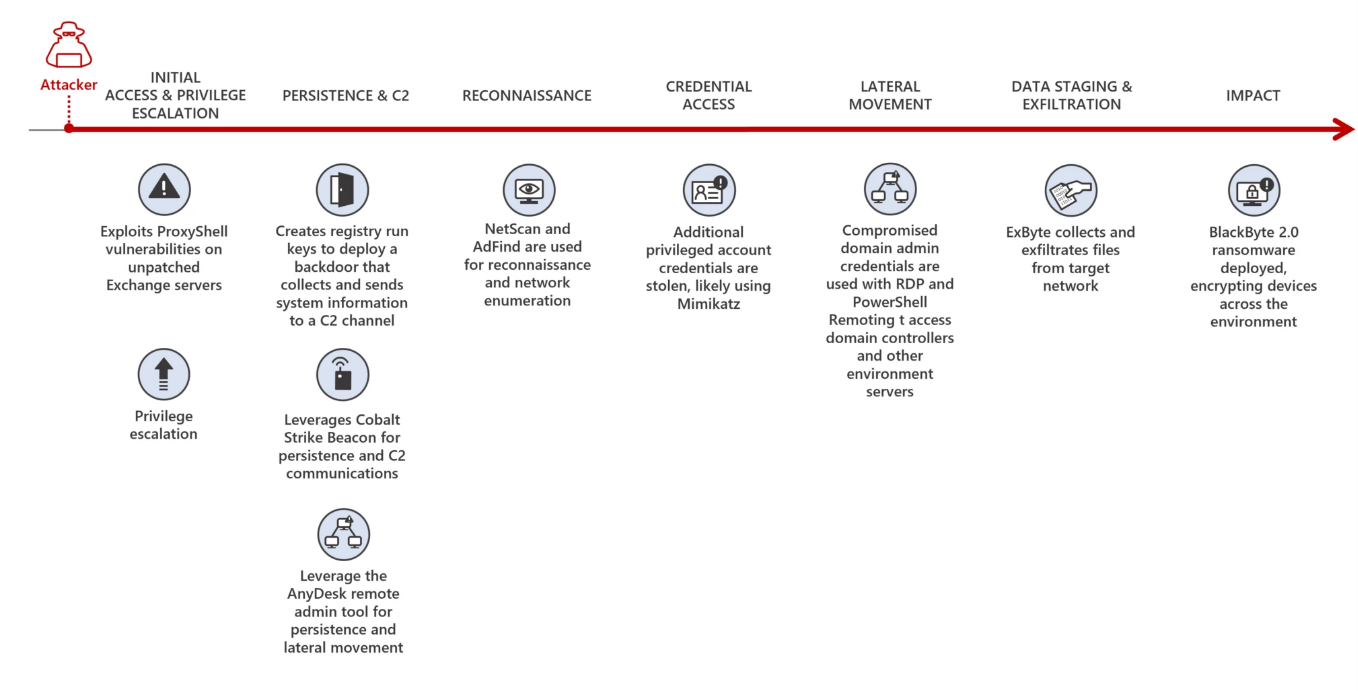
- Hackers can complete the entire attack process, including gaining access, causing damage, and demanding ransom, in just five days.
- BlackByte ransomware is used in the final stage, employing an 8-digit number key for data encryption.
- Attackers exploit unpatched Microsoft Exchange Servers to gain initial access and execute their malicious activities.
- Process hollowing and antivirus evasion techniques ensure successful encryption and evade detection.
- Web shells provide remote access and control to maintain a presence within compromised systems.
- Cobalt Strike beacons facilitate command and control operations, making defense more challenging.
- "Living-off-the-land" tools are used to blend in with legitimate processes and avoid detection.
- Volume shadow copies are modified to prevent data recovery through system restore points.
- Specially-crafted backdoors ensure continued access for attackers after the initial compromise.
Recommendations:
- Implement robust patch management procedures to timely apply critical security updates.
- Enable tamper protection to strengthen security solutions against bypass or disable attempts.
Indicators of Compromise :
Find some of IOCs below
| Indicator | Type | Description |
| 4a066569113a569... | SHA-256 | api-msvc.dll |
| 5f37b85687780c0... | SHA-256 | sys.exe |
| 01aa278b07b58dc... | SHA-256 | rENEgOtiAtES |
| ba3ec3f445683d0... | SHA-256 | [RANDOM_NAME].exe |
Conclusion:
The escalating threat of ransomware attacks demands immediate action from organizations worldwide. Microsoft's investigation into BlackByte 2.0 highlights the rapidity and severity of these attacks. Implementing recommended measures, such as patch management and tamper protection, is crucial to defend against such cyber threats.
Reference :
https://thehackernews.com/2023/07/blackbyte-20-ransomware-infiltrate.html

