Almost every industry currently faces the challenge of Operational Technology (OT) cybersecurity. Maintenance of OT security has become progressively difficult due to factors like aging hardware, integrated proprietary software, 24/7 operations, etc.
The Medical Devices industry is no different than the rest. In the production of medicines and devices, these difficulties are sometimes made worse by regulatory restrictions and threats to patient safety and private information.
Obstacles encountered by medical devices manufacturers
Manufacturers of medical devices must overcome several challenges on a day-to-day basis and it never gets easier. The production process of many contemporary medical devices involves handling sensitive information, which carries a risk from both a security and compliance perspective. Also, the devices themselves represent significant intellectual property for many operators. Unlike commercial systems, the control systems of medical devices were frequently created ten to thirty years ago, without the same level of documentation or change management. Moreover, careful consideration must be given to the operating systems of medical devices and the data they handle since they present unique security issues. Finally, developing industrial equipment and internal control systems often involves managing internal development teams as well. To guarantee the security and compliance of medical devices, these issues need to be taken into account and resolved.
What are some potential consequences to be on the lookout for?
In the modern age of technology, medical devices have become increasingly vulnerable to cyber-attacks. Hackers can use these devices as entry points to target the entire network of a hospital, leading to the exposure of sensitive patient data. It is imperative to utilize up-to-date and cost-efficient components in the manufacturing process to enhance security. Additionally, protocols that are less secure than industry standards can put protected health information (PHI) at risk of exposure, so it is important to prioritize security measures such as the sanitization of operational data. To maintain compliance with security standards, regular security audits, both physical and remote should be conducted to ensure the safe operation of the hospital's network.
Threats to medical devices OT:
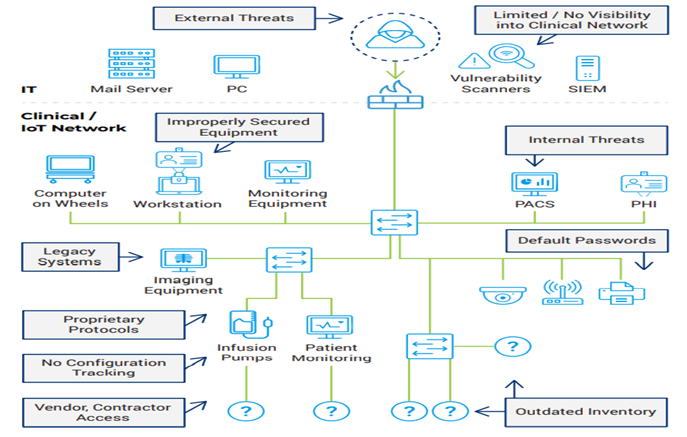
External Threats:
Malicious Actors with motivation to affect Healthcare Delivery Organizations.
- Malware and Phishing Attempts
- Botnets
- Credential Harvesting
Internal Threats:
Internal threat actors with intent to sabotage the production.
- Privilege escalation
- Remote access
- Network Protocols
Insecure Equipment:
Due to certification or availability constraints, many medical devices cannot be patched.
- Legacy systems
- Default Passwords
- Outdated hardware
Recent attacks on the medical OT environment:
Missouri Delta Medical Center ended up compromising the confidential information of 95,000 patients after they fell victim to a cyberattack on September 9, 2021. The incident was later found to be committed by a notorious hacking group Hive ransomware, responsible for various attacks on the healthcare sector. Hive employs phishing emails to target its victims and once it gains access to the network, Remote Desktop Protocol (RDP) is used to navigate through the network.
Reference: THE LYON FIRM
Securing medical OT: Transition toward a secure environment
The image below provides guidelines for Medical Device OT Security based on various Industry Frameworks
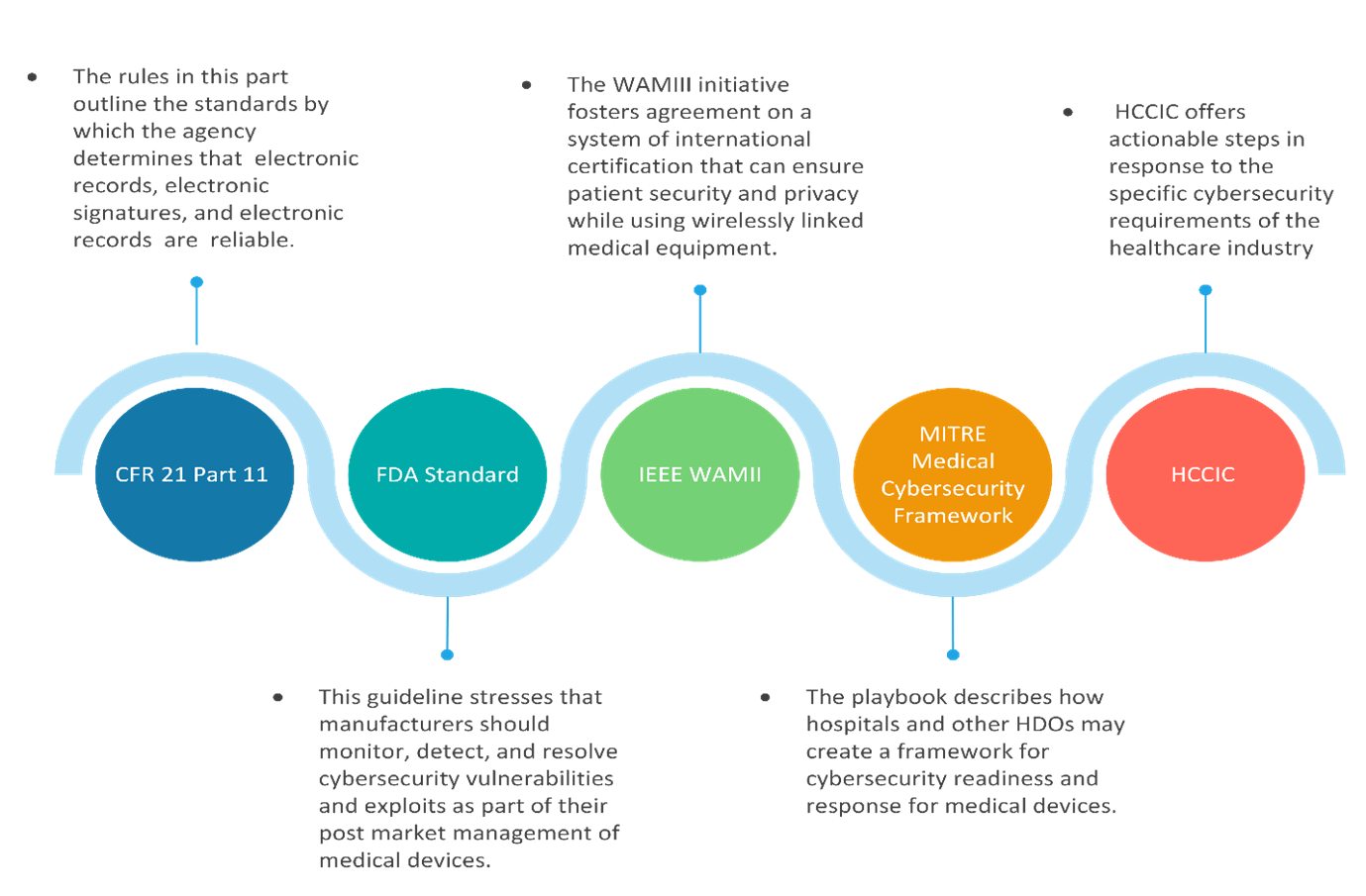
Based on the above standards, the following are a few measures organizations can take to improve their Security posture.
- Separate logical and physical networks at sites.
- Boost the security of perimeter devices.
- Deploy application “allow lists”
- Threat detection services to monitor USB media on the OT network.
- Administering 24/7 threat monitoring to detect any unusual activities and promptly alerting in case of detection.
- Industrial Demilitarized Zone (IDMZ) for sites.
- Physical installation, cabling, and Services for the deployment of Supervisory Control and Data Acquisition (SCADA) systems.
- Implementation of a Managed Services program to monitor and manage the network, data centers, and applications.
Need some assistance for the safety of your organization? Take a look at our MSSP services

