The scalability, flexibility, and cost-efficiency offered by cloud computing have revolutionized the way businesses operate. However, these benefits come with new challenges, particularly in terms of securing sensitive information from an ever-expanding array of cyber threats.
This is where cloud security monitoring comes in – a robust approach that enables organizations to proactively safeguard their cloud assets and ensure the integrity, confidentiality, and availability of their critical data. In this blog post, we will explore the significance of monitoring in the context of cloud security, emphasizing how this practice plays a pivotal role in mitigating risks and fortifying the resilience of cloud environments.
What does cloud security monitoring exactly do?
From real-time threat detection and incident response to compliance adherence and anomaly identification, cloud security monitoring equips businesses with the necessary visibility and control needed to navigate the complex security landscape of the cloud. Through continuous monitoring, organizations gain valuable insights into the behaviour of their cloud infrastructure, enabling them to identify vulnerabilities, spot suspicious activities, and fortify their defences before potential threats escalate.
In what manner does Positka's cloud security monitoring solution integrate within the context?
Positka's Cloud Security Monitoring Solution offers a valuable tool for security teams, enabling them to monitor their security operations regardless of their organization's size or level of expertise. By ingesting data from the cloud platform and various services within the platform, the solution provides valuable insights. It employs correlation rules that generate alerts, facilitating the rapid detection and analysis of advanced threats. This approach allows for heightened operational visibility without adding complexity to existing systems. Additionally, the solution offers flexibility in customising dashboards, reports, and correlation searches, catering to the specific needs of continuous monitoring and incident response teams who require a comprehensive view of risks occurring in the cloud. With its analytics-driven security approach, Positka's solution uncovers relationships within all security-relevant data, adapting to the ever-changing threat landscape and ensuring robust protection.
Let's explore few of the capabilities/features offered by the solution.
Single pane of glass visibility:
Positka's Cloud Security Monitoring solution for cloud services provides an effortless experience in configuring and monitoring all cloud platform logs from AWS, Azure and GCP across services like Network, Compute, Storage and IAM.
Benefits include:
- Gathering important insights into security-related activities such as unauthorized access attempts, network configuration changes.
- Increased visibility into user behaviour and resource utilisation.
- Audit trail logging improves adherence to security and compliance requirements.
Using this solution makes it easier to visualize and consume data for developers, system administrators and security professionals under one easy-to-manage interface.
Security posture dashboard:
The Security Posture Dashboard gives a consolidated view of key metrics, making it easier for the organization to make key decisions. This security posture helps to understand what has happened across the cloud environment and helps determine if a cloud resource might have been compromised.
Incident response workflow:
- Optimise incident response workflows by utilising the integrated incident response workflow.
- Assign and track alerts from inception to remediation and closure.
Security analytics view:
The Security Analytics view helps conduct rapid investigations using ad hoc searches, as well as static, dynamic and visual correlations to investigate threats or attacks happening in the cloud environment. Get insights with actionable information to reduce risk, threat context and track attacker steps to verify evidence.
Service overview activity pane:
- The Security Overview dashboards provide detailed information about the activity happening within specific service in your cloud environment.
- It also contains multiple filters to help drill down into specific resources to be investigated.
Use case library/alerts:
A sophisticated library of use cases across services helps drive real-time monitoring for threats. Use cases comprise alerts (rules) and corresponding dashboards, which help security analysts to quickly investigate potential incidents.
Why Positka’s cloud security monitoring solution?
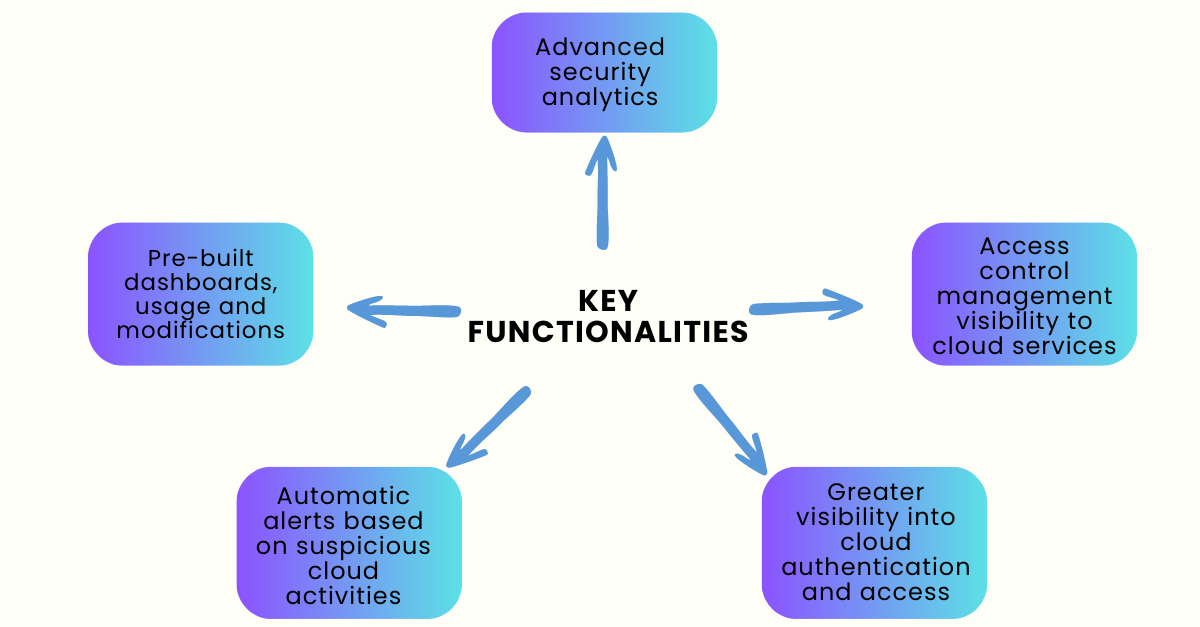
FAQs:
What are the common threats to cloud security?
Common threats to cloud security include data breaches, unauthorized access, insider threats, insecure APIs, misconfiguration of cloud services, denial-of-service (DoS) attacks, and malware infections. Cloud security monitoring helps organizations stay vigilant against these threats and take appropriate actions to mitigate them.
How can I ensure compliance with regulatory requirements in the cloud?
To ensure compliance with regulatory requirements in the cloud, organizations should implement appropriate security controls, conduct regular audits and assessments, and leverage cloud security monitoring tools. They should also stay informed about relevant regulations and standards, such as GDPR, HIPAA, PCI DSS, and ISO 27001, and adopt cloud services and configurations that align with these requirements.
Protect your data with proactive cloud security monitoring. Start securing your cloud environment starting with scheduling a demo!

